Authentication vs identification
Learn the difference between identification, verification, and authentication. Understanding these concepts is crucial as they impact privacy, security, and access control. This article explains these differences, why they matter, and when to use each term.

What is the difference between identification vs authentication?
Identification is the process of recognising a user. It’s essentially a claim of identity i.e. a user stating “This is who I am”.
Authentication is the process of verifying the claimed identity of a user. This involves the user presenting credentials that they have under their sole control such as a password, biometric data (like fingerprint or facial recognition), security token or a cryptographic key. The system then verifies these credentials against stored records to confirm the user’s identity.
In other words, authentication answers the question, “Are you really who you claim to be?”

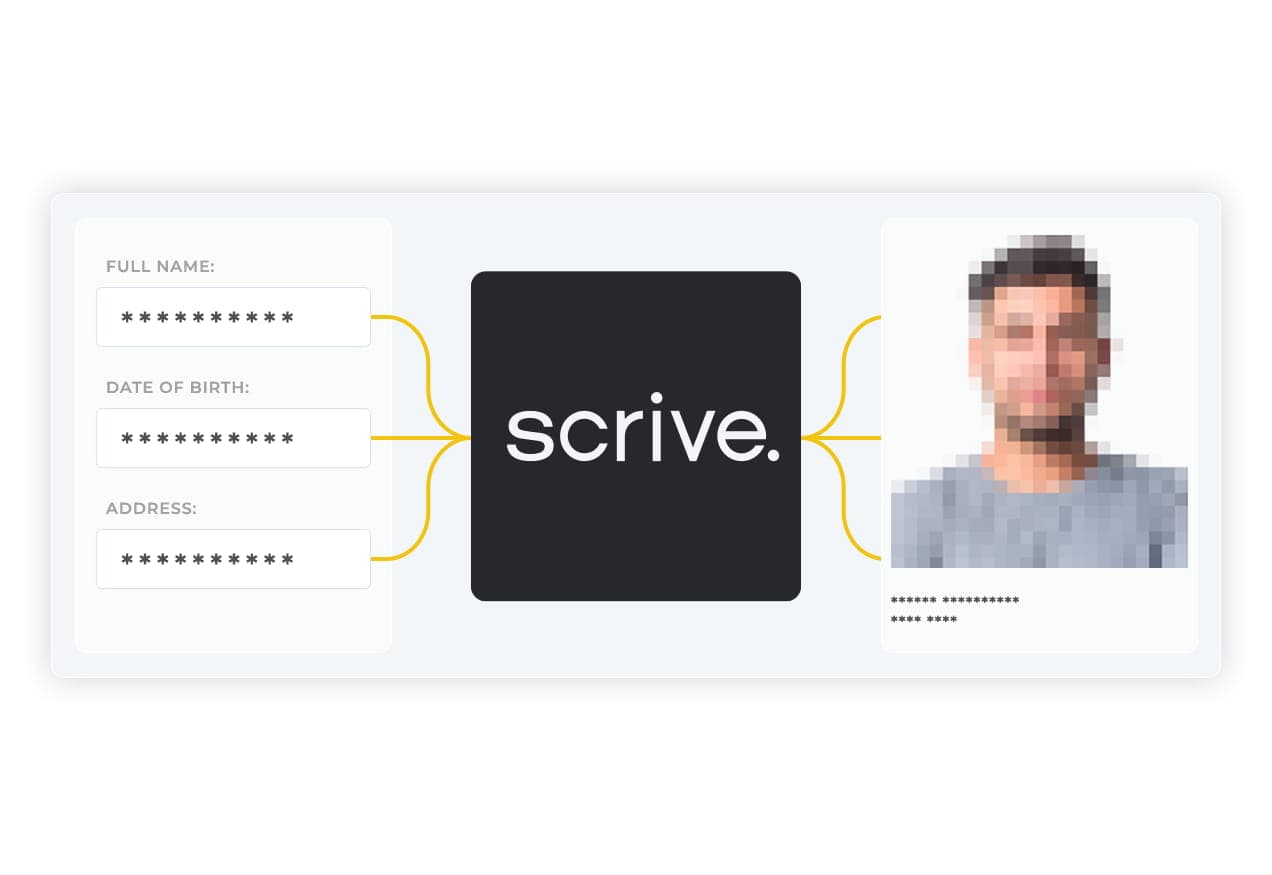
Improving user Identification and Authentication with Scrive’s eID Hub
By using Scrive’s eID Hub you can identify the users of your systems and then authenticate them via eID verification.
According to the eIDAS regulation, authentication is defined in levels of assurance (LoA). These range from Low, Substantial, to High. Most eIDs provide at least the substantial level of authentication, with some reaching the high level.
For example, when a user logs on to a system by entering a user ID and password, the user ID is used to identify the user. The system authenticates the user by checking that the supplied password is correct when the user attempts to log in.
The importance of authentication
Verifying the identity of a user or customer is essential for several reasons. Whether they are accessing sensitive information, age-restricted items or content, or if your business needs to meet regulatory requirements by gathering specific customer or user information, authentication plays a vital role.
In industries like banking and finance, KYC and AML regulations, sanctions, and PEP checks are common concerns. Regulatory compliance in these industries not only involves large sums of money but also significantly impacts organizational reputation and the bottom line.
Moreover, providing your customers with peace of mind when using your services is an incredibly effective way to build and maintain trusted relationships.

Utilising different factors of authentication:
When talking about multi-factor authentication, these factors refer to different ways of identity verification. Typically these are split into something:
- you know (e.g. password/personal identification number (PIN))
- something you have (e.g., cryptographic identification device, token)
- or something you are (e.g., biometric).
A well-known example is the two-factor authentication (2FA) method used by banks. You log in with a username and password (something you know), then confirm your identity with a token or key fob (something you have).
In regions like the Nordics and Baltics, companies and banks are using eIDs for this purpose. Scrive provides several methods to implement eID authentication.
Various authentication factors
Enhance signing security with eID Authentication
If you want to authenticate within a signing process, you can integrate eID verification into your eSign Online or eSign GO instance.
- For example, you can request authentication when signing a document to ensure you can identify the signer and have evidence to support it. Additionally, if a document contains sensitive information, you can include an authentication step to access it.
Simplify customer Login with eID Hub
If you’re looking to enable your customers to log in using eIDs, our eID Hub is the one stop shop for all of your eID needs.
- For instance, if you want to provide an easy way for your customers to sign into sections such as “My pages,” a common feature on real estate company websites, telecom websites et.c , you can offer eIDs as a single-sign-on solution.
Customise your integration with our API
If you’ve got more specific or niche requirements, our API is your best bet.
- For example, if you’re connecting multiple systems seamlessly, you would probably choose our API.
Securely gather information with ID verification in Web Forms
If you’re looking to securely gather information and verify the sender of said information, integrating ID verification in our web forms solutions should suit your needs.
- For example, if you’ve got a publicly available form and want to ensure it’s not being submitted by bots or malicious actors, you can require authentication at delivery. Alternatively, if you need to ensure the information is verifiable and trackable to an individual in a secure, compliant way, the same solution would work perfectly.
Conclusion
Now that you understand more about authentication, identification, and ID verification, what should you do next? Depending on your objectives, it might be beneficial to explore how you can implement these practices within your organisation. If you have ideas or need help, please reach out. We will assist you in your digitalisation journey. Want to know more about authentication? Read our guide about authentication in EU